
Company News
Written on 16.02.23
With the emergence of remote and hybrid working, a new security model has arisen – Zero Trust, as the old digital security archetype has seemed to have become archaic in comparison, considering today’s challenges with securing infrastructure and data for digital transformation, within this new working environment.
There is no universal definition for zero trust, however it does assume that no user, device, or service can be trusted – minimising IT risks for organisations by granting the lowest possible authorisations and access only when necessary. It isn’t a product or software, but rather a set of principles for organisations to interpret as they see fit and follows on from a trend set by industry and market leaders, Microsoft and Google.
Zero trust incorporates the following security structure:
Before access is allowed, authentication and authorisation on all data points should be strictly enforced.
The requester must be rigorously evaluated before being given limited access needed to complete a task, with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
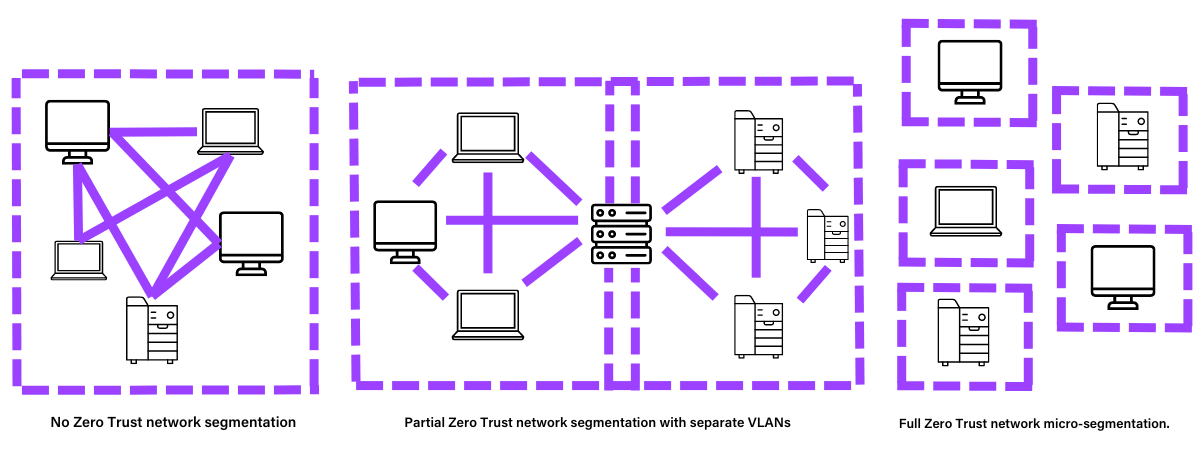
Blast radius and segment access should be minimised, as if an attacker is present on the enterprise network, by verifying end-to-end encryption and using analytics to get visibility, drive threat detection, and improve defences.
While preventing bad actors from gaining access is critical, it’s only part of the Zero Trust equation. For businesses looking to become more resilient in the face of cyber threats, printing and scanning should also be taken into consideration as a part of the security model overall, as an organisation’s most valiant efforts could all be in vain without it, and things could fall apart quite rapidly. Attackers can use printers as an inconspicuous access point from which to gain access to an organisation, as well as the information processed by printers being targeted from inside or outside an IT environment.
Usually, PCs and printers are all linked to the same network or split into different virtual networks (VLANs) with a printer server bridging the gap. However, by utilising the zero-trust concept, all network end points are isolated from each other as much as possible. This means that should one PC become infected or compromised, it cannot ‘talk’ or spread to any other. IT risks can also be further minimised by only allowing internet access from an internal network.
Although, there are many advantages to remote and hybrid working, such as the fluidity between people’s work and personal lives, this also opens up a new arena of entry points for attacks to identities, devices, apps, networks, infrastructure, and data, that live outside the protections of traditional perimeters. Therefore, any company that wants to protect their business-critical data, especially within an environment of remote and hybrid working should operate with a zero-trust mentality. It also has the added benefit of companies being able to streamline costs by ridding themselves of their local on-premises infrastructure, which effectively would be made redundant by the zero-trust model.
For more information on how Aurora can help you to adopt more secure printing practices, visit us here, call us on 020 7503 3000 or e-mail generalenquiries@aurora.co.uk